ClearSCADA has two security mechanisms: user accounts and database item permissions. Typically, each system user is allocated a user account. The features that are available to the user depend on the configuration of their user account and the security settings of the items in the database.

When a user accesses ClearSCADA, they either log on manually or are logged on automatically using one of the following:
- A ‘configured’ user account—A user account that has been created manually and configured to have a username and password and used log on to ClearSCADA via ViewX, WebX and third party clients that support secure user access.
NOTE: Users accessing the database using ASB Framework Services have to use a configured user account to log on and should have security settings configured to their requirements.
- The built-in Guest user account—The default account that is used when users access ClearSCADA via ViewX, OPC, ODBC and Automation without logging on. By default this account is inactive and does not provide accesses to the database (see Guest User Account).
- The built-in Web user account—The default account that is used when users access ClearSCADA via a web interface (such as Original WebX) without logging on, (see WebX Client).
NOTE: WebX users have to use a configured user account to log on.
‘Configured’ user accounts are regarded as a more secure way of accessing your system as they require manual entry of a user name and password (see User Accounts for System Users).
The items and features that a user can access are determined by:
- The permissions allocated to the ‘Everyone’ User Group
- The permissions allocated to any User Group of which the user account is a member
- The permissions allocated to the individual user account
- The configuration of the individual user account.
Example:
If you access the security settings for a Mimic, you can allocate the Configure permission to a user account or the user group associated with the user account. The user of the account has the Configure permission that allows access to the Mimic configuration features. However, the user will only be able to configure the Mimic in ViewX if the user account also has the Configure Documents feature enabled.
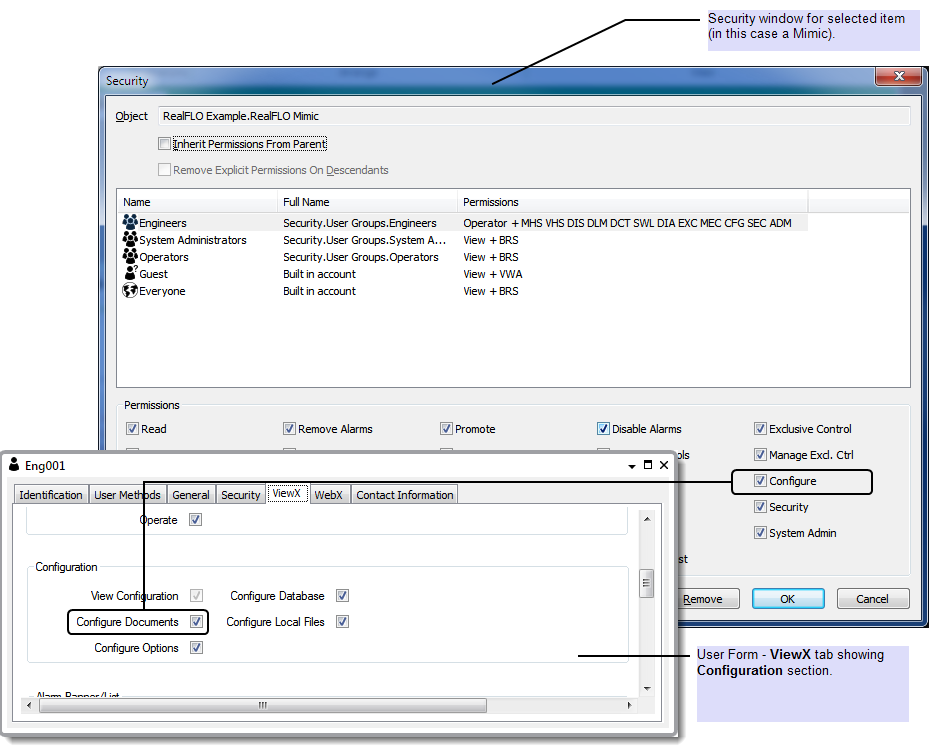
To access ViewX features such as the configuration options, user accounts need to have the permissions for a database item and the relevant ViewX features enabled on their User Forms (see User Accounts).
NOTE: User Groups and user accounts are only applicable if Security is enabled. You can enable Security by using the Server Configuration Tool (see Define whether any Permissions are Restricted).